Edge Computing: How to Customize Your Servers
In today’s fast-paced digital world, more and more of us are feeling the crunch. Ever thought about how your favorite app loads in a heartbeat, while that simple webpage takes ages to navigate? You’re not alone. Many of us share similar frustrations. As we rely more on technology, the demand for faster processing speeds and immediate responses has never been higher. It’s not just about speed, though; it’s about where data is processed. This is where edge computing comes into play, and it’s time we dive deep into it. So, what is edge computing, and how can you customize your servers for maximum efficiency? Well, worry not, because we’ve got you covered!
Edge computing is a game-changer. Think of it like having a coffee shop right around the corner instead of having to travel miles to the closest mall for a fancy café experience. In computing, edge means getting data processed closer to where it’s generated rather than relying on far-off data centers. This technology has become essential, especially in a world where remote working and online interactions dominate our routines. Let’s explore how you can tailor your servers to maximize this innovation.
Understanding Edge Computing
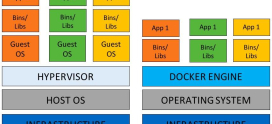
Before we delve into customization, let’s clarify edge computing. In simple terms, edge computing brings computational power closer to where data is generated or used, enhancing speed and efficiency. Rather than sending data back and forth to distant servers, edge computing processes it on-site or in localized servers. This means faster response times and less strain on bandwidth.
The Benefits of Edge Computing
- Speed: Faster data processing means less lag, which is crucial for applications that require real-time responses, like online gaming and video streaming.
- Bandwidth Optimization: Reducing the amount of data sent to central servers saves bandwidth, which translates to lower costs.
- Enhanced Security: By localizing data processing, sensitive information can remain closer to its source, minimizing exposure to cyber threats.
The Basics of Customizing Your Servers
Now that we understand what edge computing is, let’s talk about customizing your servers. Customization isn’t just for tech gurus; it’s for anyone who understands the need for speed and efficiency. Think of it like customizing your car. You wouldn’t settle for a plain vehicle when you could have one suited to your tastes and needs, right?
Assess Your Needs
The first step in customizing your servers is to assess what exactly you need. Are you running a small business? Or are you part of a larger enterprise handling massive amounts of data? Your requirements will differ based on your operations. For instance, businesses heavily reliant on real-time data analytics will benefit more from edge solutions than others.
Choose the Right Hardware
Not all servers are created equal. When selecting hardware for your edge computing setup, consider factors such as:
- Processing Power: Faster processors mean quicker data handling.
- Storage: Opt for solutions that allow for easy expansion.
- Climate Tolerance: If your edge devices are in less-controlled environments, ensure they can withstand those conditions.
Networking at the Edge
Your network infrastructure plays a pivotal role in the success of your edge computing strategy. A reliable, high-speed internet connection is non-negotiable. Think of it this way: if your network is like a highway, the last thing you want is a traffic jam slowing down all your vehicles.
Implementing 5G Technology
5G technology is designed for the future. With faster speeds and lower latency, implementing 5G can significantly enhance your edge computing capabilities. By enabling more devices to connect simultaneously and transferring vast amounts of data quickly, 5G helps you make real-time decisions that can adapt to changing needs.
Integrating Security Measures
In an age of heightened security concerns, protecting your data is paramount. As your servers are closest to the action, they are also more vulnerable to threats. Integrating robust security measures is not merely an option; it’s a necessity.
Best Practices for Edge Security
- Encryption: Ensure all data transmitted is encrypted to prevent unauthorized access.
- Regular Updates: Keep your firmware and software up to date to guard against vulnerabilities.
- Access Controls: Limit who can access critical systems and data based on roles.
Choosing the Right Provider: A Case Study
It’s essential to align with a service provider that understands your needs. One suitable option is DarazHost, renowned for its edge computing solutions. Let’s examine a case study where a manufacturing company migrated to edge computing with DarazHost’s assistance.
The Success of ABC Manufacturing
ABC Manufacturing faced significant delays in its supply chain operations due to inefficient data processing. After partnering with DarazHost, they adopted an edge computing model that enhanced their data processing speed by 40%. The real-time analytics provided insights that enabled them to optimize inventory levels and streamline production, vastly improving their overall efficiency.
Monitoring and Maintenance
Customizing your server isn’t just a one-and-done deal. Regular monitoring and maintenance are crucial to ensure optimal performance. While it may feel tedious, think of it like regular check-ups for your health. Ignoring the little signs can lead to bigger issues later.
Utilizing Monitoring Tools
Investing in server monitoring tools can provide insights into performance issues before they escalate. Monitoring tools can help track:
- Data usage and throughput
- Server health and uptime
- Potential security breaches
Embracing Future Innovations
The world of technology is ever-evolving, and so is edge computing. Keeping an eye on future innovations can further enhance your server’s performance. Artificial Intelligence (AI) and Machine Learning (ML) are slowly being integrated into edge systems, providing predictive analysis and proactive decision-making capabilities.
Stay Updated
Subscribe to tech news sites and follow advancements in your industry. Engaging with communities can also provide valuable insights, tips, and tricks from others exploring similar paths.
FAQs
What is edge computing?
Edge computing is a distributed computing framework that brings computation and data storage closer to the sources of data, reducing latency and bandwidth use.
How does edge computing improve security?
By processing data locally or closer to its source, edge computing minimizes the amount of sensitive data transmitted over networks, reducing risks of interception.
How do I know if edge computing is right for my business?
If your business requires quick data processing, high reliability, or deals with large amounts of data, edge computing can provide significant benefits.
Can I implement edge computing on my own?
While it’s possible to set up edge computing independently, consulting with experts like DarazHost can streamline the process and ensure you’re getting the most of your setup.
What types of applications benefit the most from edge computing?
Applications requiring real-time processing, like video streaming, online gaming, IoT devices, and manufacturing automation, benefit significantly from edge computing.
What are the risks of edge computing?
Edge computing can introduce certain risks, including:
– **Complexity of Management:** Managing multiple edge devices and systems can be more complex than centralized data processing, requiring specialized knowledge and skills.
– **Security Vulnerabilities:** While localized data processing can enhance security, the edge devices themselves can become targets for cyber attacks if not properly secured.
– **Inconsistent Performance:** Depending on the network connection and device capabilities, the performance of edge computing can vary, leading to potential inconsistency in user experience.
– **Dependency on Local Infrastructure:** If local infrastructure fails for any reason (e.g., power outage, hardware failure), it can disrupt data processing and application availability.
while edge computing offers numerous advantages, it is essential to weigh these against the potential risks and implement effective strategies to mitigate them.